Wireshark CTFs | Writeup | TryHackMe - Part 1 of 2
Part one of a two part writeup on Wireshark CTFs room at TryHackMe. Join me in solving this packet capture analysis challenge together step by step using Wireshark

This is my very first CTF related writeup. Feel free to leave any comments down in the Disqus chat so I can improve in future articles 🙂
Origins
Recently I have been researching and learning a lot about Information Security, Networking and Capture The Flags.
As usual, I found some good stuff going down the rabbit hole.
This time, I stumbled upon TryHackMe and here we are talking about it.
TryHackMe is a cyber security training/learning platform like the venerable pentesting labs platform HackTheBox. However, TryHackMe is more oriented towards people who are learning are considered newbies of CyberSec although they do have some diffucult rooms as well.

How TryHackMe works is that there are paid rooms available only to subscribers ( students get huge discounts) and free rooms as well. There are many free rooms of which the quality is kind of amazing so do not belittle these free rooms. All the deployed vms in the rooms are accessible only through OpenVPN and each user has their own machines. If you have ever tried to hack a box to get a flag but realised some bugger has gotten ahead of you and deleted the flag, you would very much love this.
TryHackMe Advent

Back to the story, I found TryHackMe on Reddit where they were advertising their Christmas Advent event where its tailor entirely for beginners to learn the ropes so to speak, with new challenges everyday and relevant material given to solve the challenges. They do have a leaderboard but it is not really used, rather, there will be a weekly raffle where anyone who has completed or submitted any flags in the room are entered for a lucky draw with some amazing prizes.
Interested? Join the community over at https://tryhackme.com/christmas and have fun!
If you are here because you googled for wirectf room writeup, fret not, its right below!
Wireshark CTFs | Writeup

Alright alright let's dive into the writeup!
This writeup is for the room with a room code of wirectf over at https://tryhackme.com/room/wirectf
It will come in two parts, part 1 (this) will talk about Task 1 and part 2 about Task 2.
The only software we will be using is Wireshark, a packet capture / inspection tool! If you have it already installed you should be good to go, else get it over at https://www.wireshark.org/. Other than Wireshark, you will need a machine capable of executing Python 2 code, which we will need for Task 1.
Task 1 | Flag within the packets
A CTF challenge set by csaw. During this task, you will be have to inspect a pcap file (using programs such as tshark and wireshark). You will analysis the file and realise something has been... "transferred".
After downloading the provided pcap file, all we need to do is either double click it to open it in Wireshark or you can open the pcap file from within Wireshark
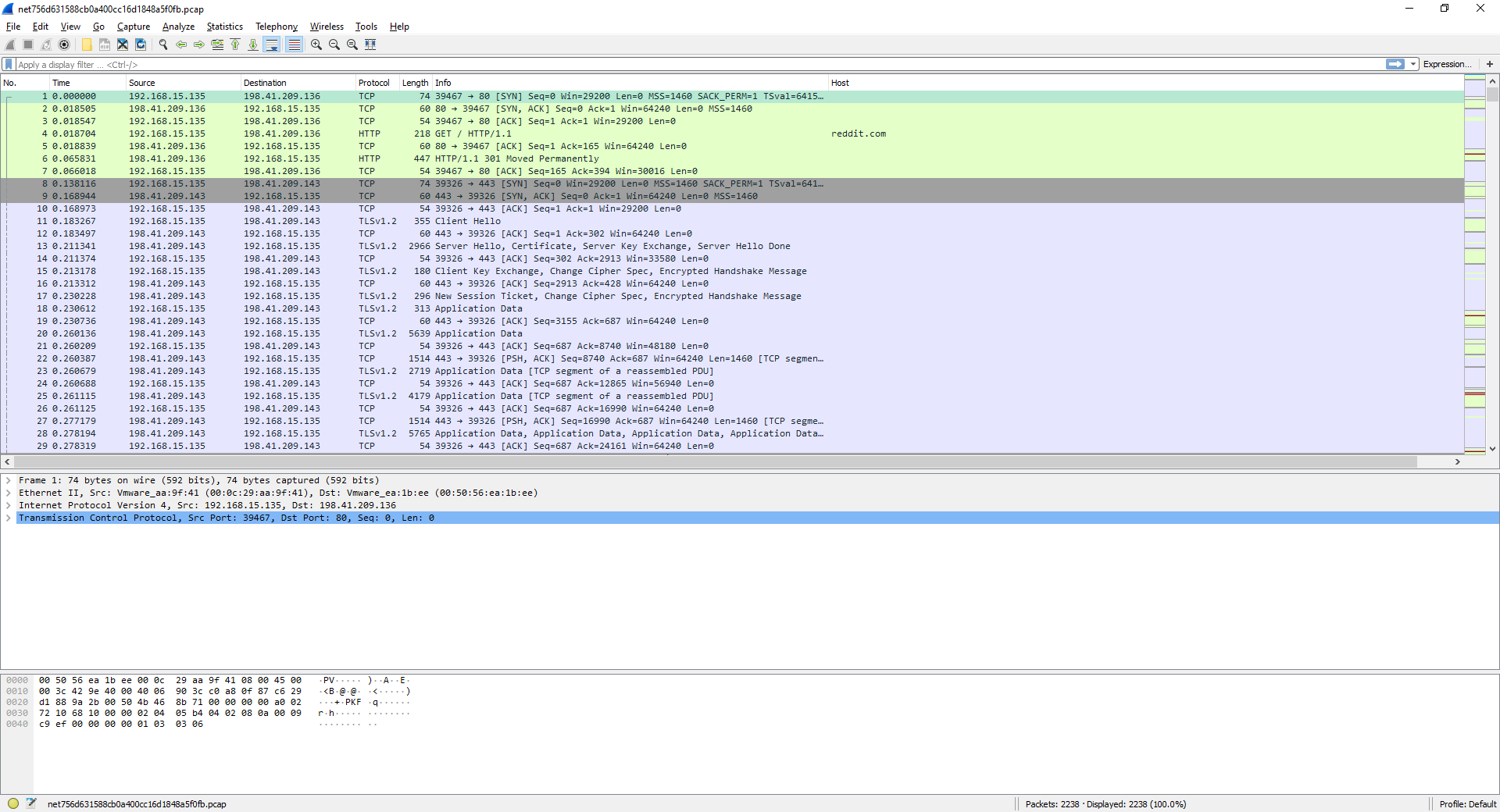
We were told that something had been transferred but it looks like that was the only clue we were given. 😢
At this point there are a few things that we can do.
- Manually inspecting the packets?
- Search for strings?
- Export objects Wireshark found?
- Have a coffee
If you want to go method 1, luckily for this particular pcap it wouldn't take that long, for most pcap challenges, it is normally recommended to do a quick inspection of the packets anyways. However, could we try the other methods?
Searching for strings would be done with Edit > 🔍Find Packet... If you want to, you could in theory search for a regex matching the answer format given in the room but where is the fun in that?
Let's try looking at the list of objects that Wireshark found on its own shall we?
We can view a list of objects Wireshark found by going to
File > Export Objects > Proctocols..
Wireshark gives us a few choices, HTTP seems to be the better option since there don't seem to be any TFTP or SMB packets in the pcap file anyways.
Once you select HTTP.. , a list like below should appear.
Those of 0 bytes serve no purpose to us. Likewise, those with hostnames that are common like Reddit or Google probably won't be what we want.
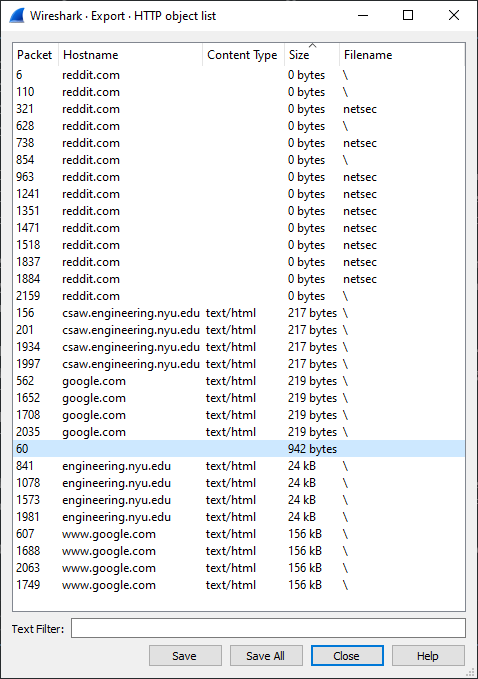
Could it be that easy? A PDU almost 1k bytes from unknown host, unknown content type and no filename. Let's take a look at it.
You can try to save that particular packet 60 but nothing will happen when you click the Save button since there is no name (at least on Windows), if you Save All, it should appear as a file named object60. I wonder what it is
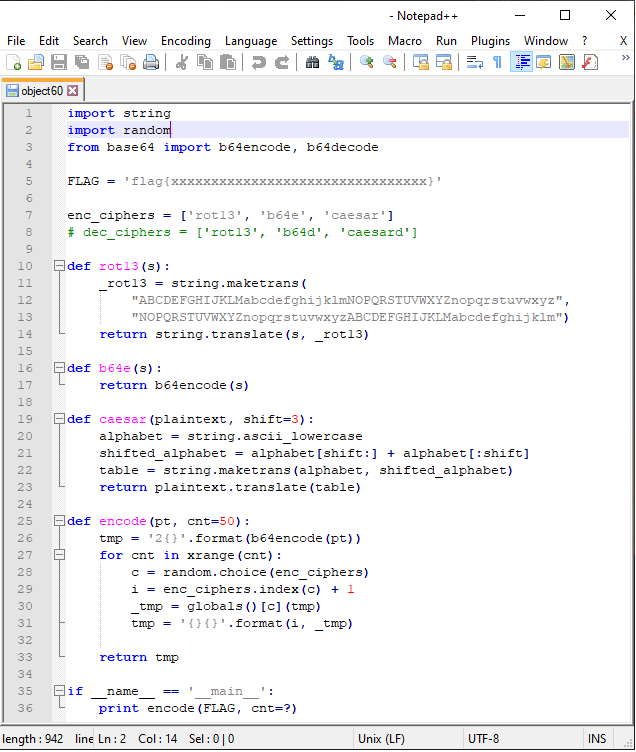
Looks like a python2 script, let's take a few minutes to read through the script and see what it does.
Basically, it is a script that was used to encode our flag. It has a main encode function that first does a base64 encoding on the initial flag and concatenates 2 in front of the output.
Next it randomly chooses between Rot13 , Base64 or Rot3 (lowercase) to encode the flag given.
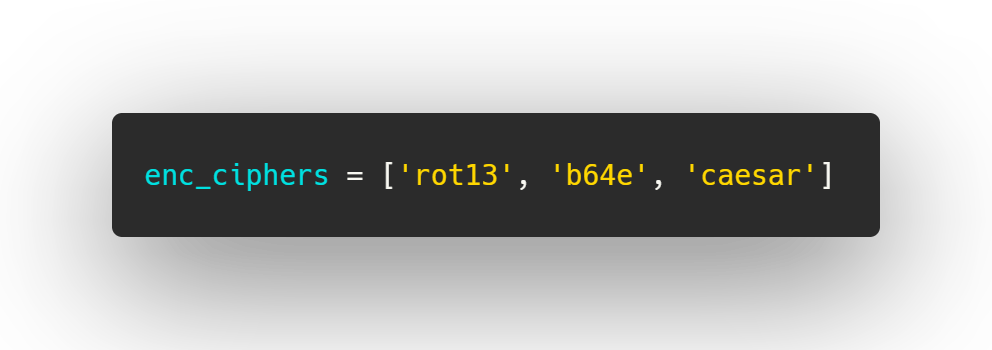
It encodes the flag for a total of cnt rounds. The output of every round is concatenated with a numerical value signifying the encoding that was used. 1 for Rot13, 2 for Base64 and 3 for Rot3 (lowercase) respectively.
We now know what we need to do, write a script to perform decoding. But where is our encoded flag?
Did we miss something? Let's go back a little.
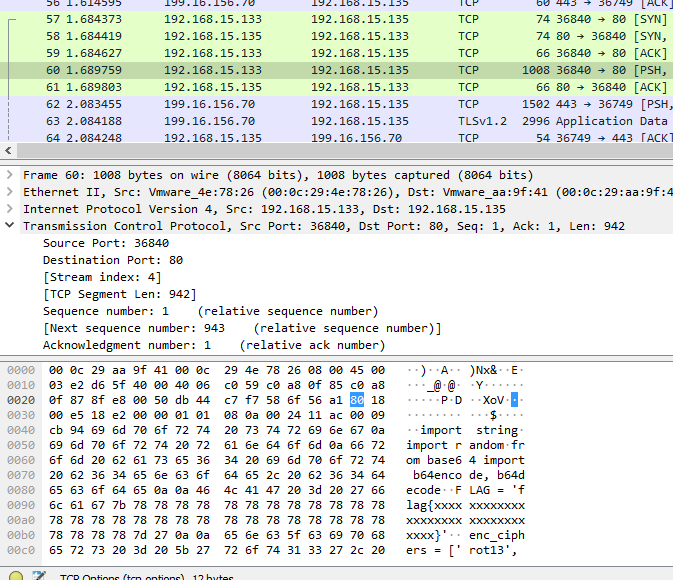
The packet by itself seems to end with our python encoding script. However, we can see it is part of a TCP stream index 4. We can follow the TCP stream by right clicking and following the TCP stream
What follows seem to be the contents of our encoding script followed by a chunk of alphanumeric junk, or is it really?
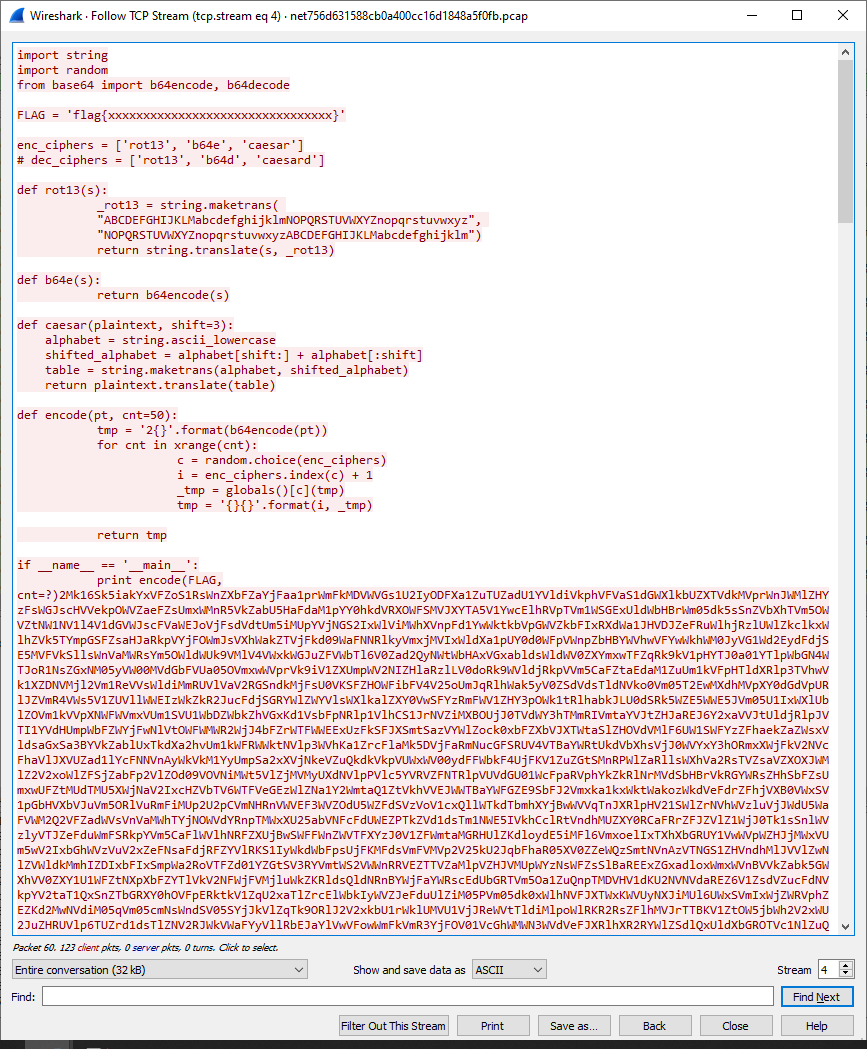
We know from reading the encoding script that the encoded flag will have the encoding method as a number at the front of the encoded flag.
Looks like it isn't junk after all. It begins with a 2 , a little verification confirms that it is able to be decoded using base64 decoding with CyberChef which gives us another long chunk of text which begins with a number.
A little scripting would be super useful here for decoding this huge text chunk it seems. Lets save the chunk as a file somewhere and get to our decoding script shall we.
We need to write some code to reverse the encoding ( Feel free to manually decode it using CyberChef if u want to 🙃). Rot13 decoding is essentially running Rot13 , Base64 has a decode function, and we can simply reverse Rot3 (lowercase) by using -3 in the caesar function.
Remember that for 3, we perform Rot-3 only on lowercase alphabet, not touching the uppercase alphabet nor any numbers.
Here is a sample code that does decoding when supplied with a file containing the encoded flag.
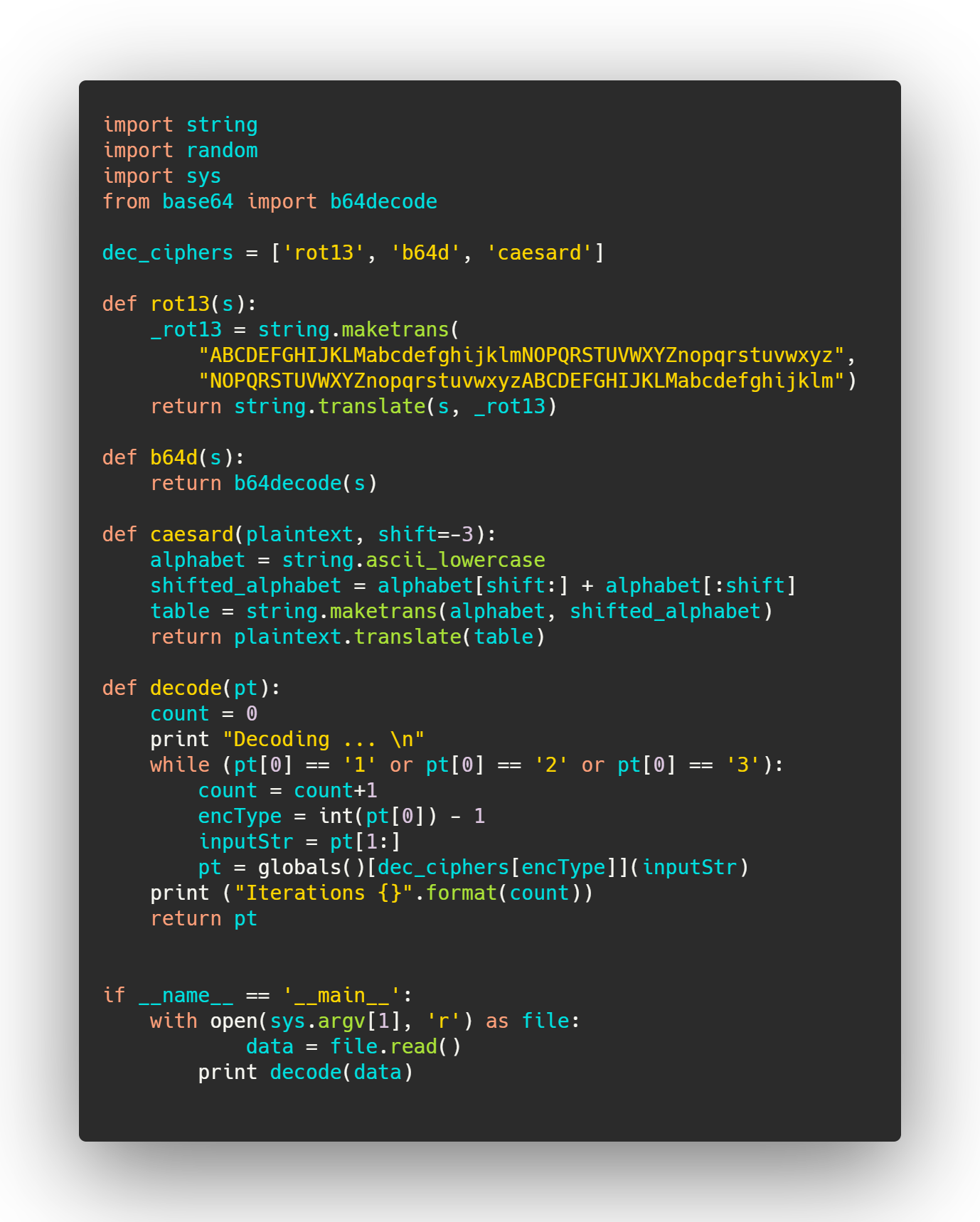
We can be sure our final result should begin with flag as given from the encoding script.
You can then run it using
python icanhazflag.py encodedflag.txt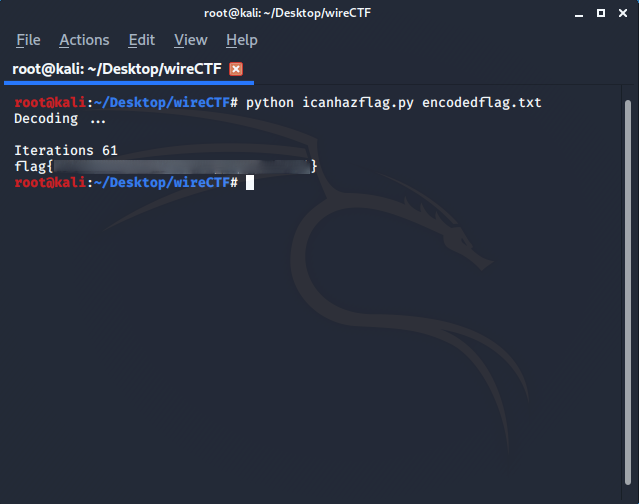
Now you have the flag, Task 1 is complete 😃
We have another Task 2 to complete but that's it for now. I hope you understand Wireshark a little better and have learnt something new.

Stay tuned to Part 2 of this writeup coming really soon.