WaniCTF 2023 | Writeup for Forensics Challenges
Writeup for all Forensic challenges in WaniCTF 2023
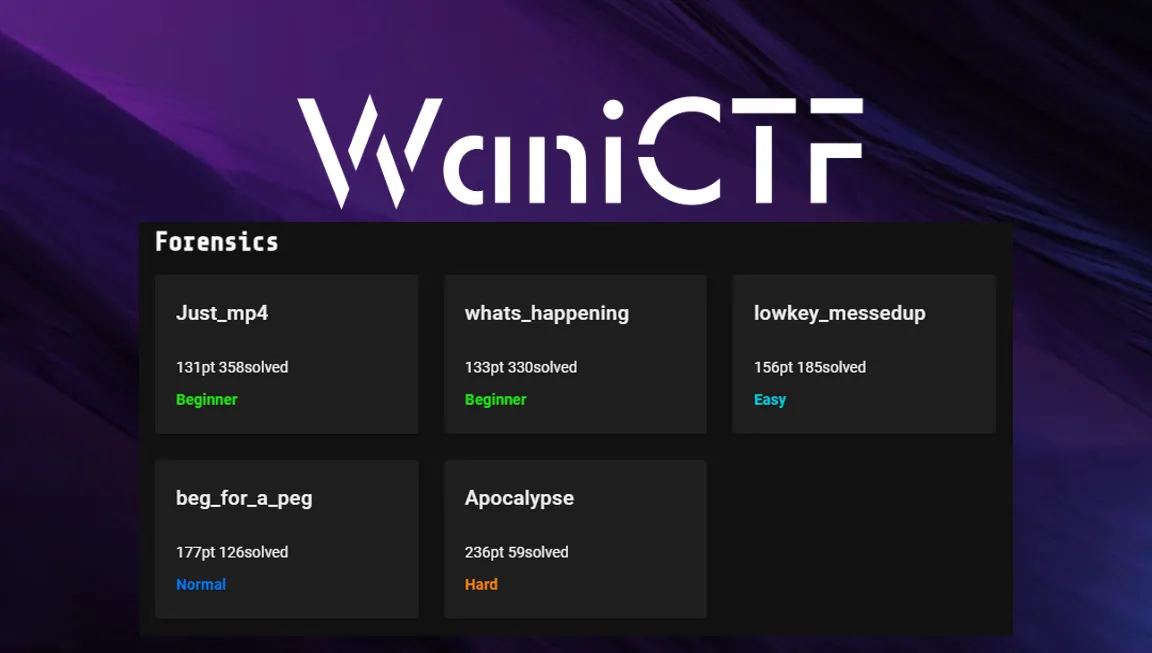
Forensics
Just_mp4
This is a beginner challenge. After downloading the mp4 file we check metadata using Exiftool
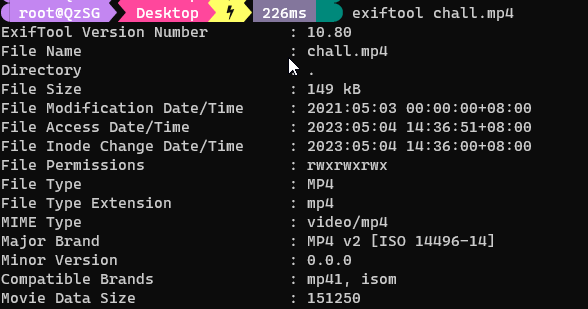
Simply check the video metadata and we have the flag in Base64 encoding.
We can chain and decode the flag in one command with
echo "$(exiftool chall.mp4 | grep flag | awk -F':' '{print $3}' | base64 -d)"
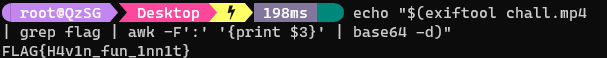
Flag: FLAG{H4v1n_fun_1nn1t}
whats_happening
You got a certain file, but it seems to be corrupted...
Should we be expecting a corrupted file?
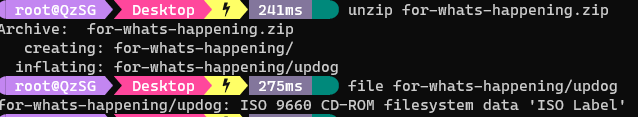
After extracting the downloading zip file and extracting it there is a updog file which we use the file utility to identify that it is a iso archive.
Extracting the iso file contents with 7z command as follows
7z x -y -ofor-whats-happening for-whats-happening/updog
We see two files FAKE_FLAG.txt and FLAG.png
Opening the png file we have the flag
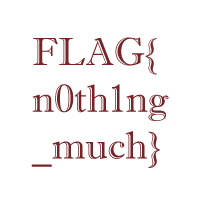
flag.pngFlag: FLAG{n0th1ng_much}
lowkey_messedup
lowkey_messedup Challenge QuestionThis challenge gives us a chall.pcap which when we open with Wireshark seems like some USB communications
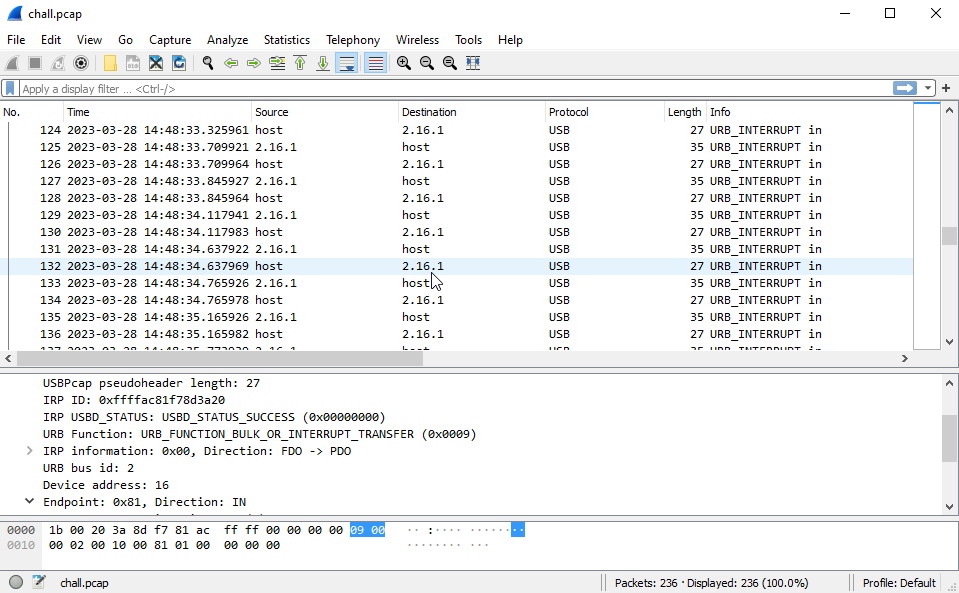
We can try to use the ctf-usb-keyboard-parser that can be found from Hacktricks
Run the following tshark command to extract the relevant usb data fields into a text file
tshark -r ./chall.pcap -Y 'usb.capdata && usb.data_len == 8' -T fields -e usb.capdata > output.txt
Running the python script with python usbkeyboard.py output.txt
We get this
FLAG{Big_br0ther_is_watching_y0ur_keyboard⌫⌫⌫⌫0ard}
Notice that the ⌫ is actually the backspace key which means
Flag: FLAG{Big_br0ther_is_watching_y0ur_keyb0ard}
beg_for_a_peg
beg_for_a_peg Challenge QuestionAfter downloading and extracting the zip file we get a log.pcapng
Opening with Wireshark we see that there is HTTP traffic, a server.html was loaded along with GET requests for a few images.
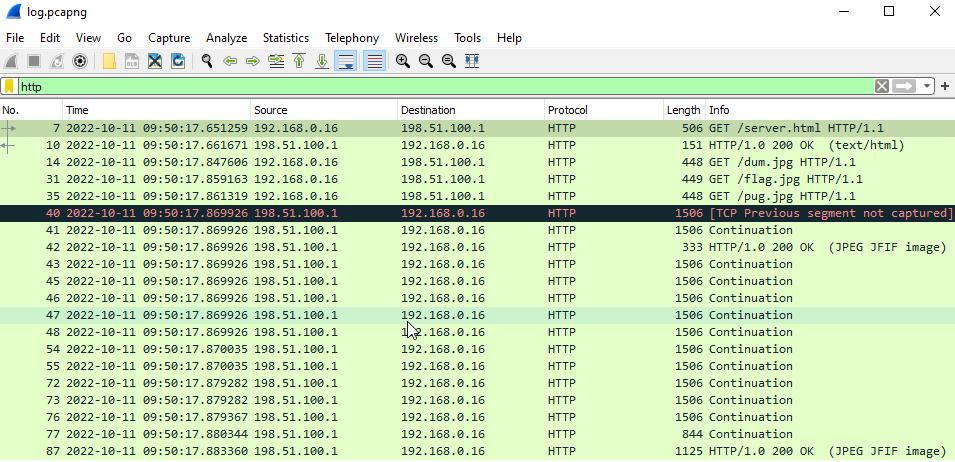
Following the TCP Stream for the GET /flag.jpg request we can see the entire TCP response as well.
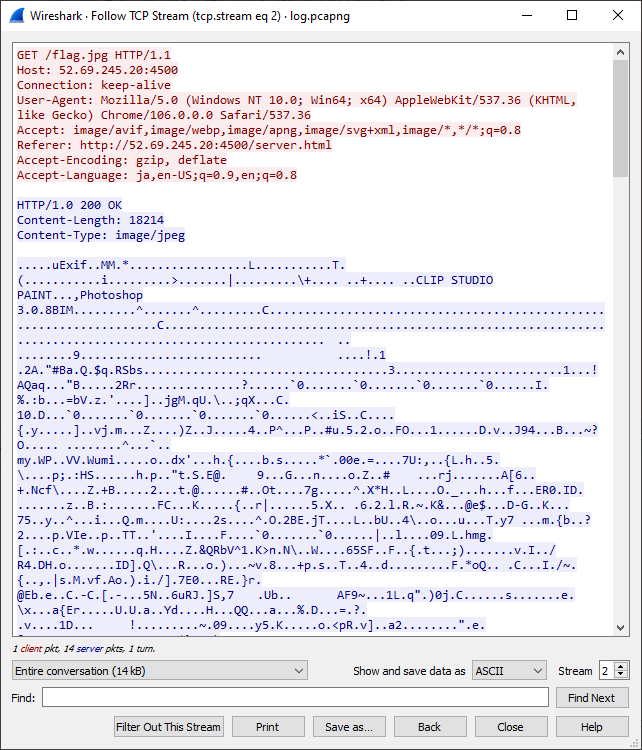
GET /flag.jpgWe export the response stream to out.raw and open it in HxD Hex Editor.
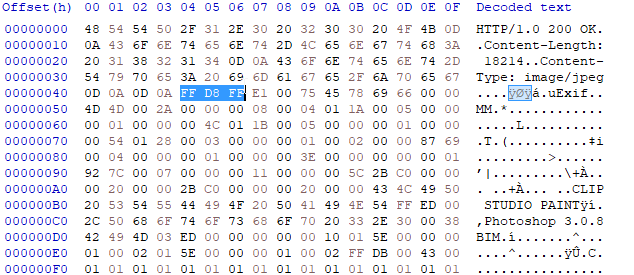
Knowing that JPG file header starts with FF D8 FF and ends with FF D9, we simply remove the front of the HTTP request and keep the image data chunk as flag.jpg

flag.jpgFLAG: FLAG{Hug_a_pug_less_than_three}
Apocalypse
Apocalypse Challenge QuestionWe get a png file that seems to be cut off but had some pixels at the bottom right which looks like some text outline.

Using (FotoForensics)[https://fotoforensics.com/]
We get the following using the Hidden Pixels Analysis option

Flag: FLAG{Watch_out_4_2023_21036}