Reflections on Syskron Security CTF 2020
This past week I have been playing in Syskron Security CTF 2020 so here are some of my personal thoughts


So this past week I have been playing in Syskron Security CTF 2020 ( Yes, instead of actually putting time into my Capstone project in school but that's another story for another day), so here are some of my personal thoughts
The CTF was actually pretty darn fun, it was spread out over an entire week, and kind of has a main theme or story crafted for the challenges, and none of them required guessing and for the most part was very doable. The duration for the entire CTF meant that I can actually play solo and get somewhere (Shameless plug that it's actually my best performance at any CTF's I have played in so far, but I could have probably done so much better on hindsight)
As usual, I was writing write ups (can be found here) for the challenges that I have solved, while solving them and it is always fun to compare them to others after the event is over to see the different ways of solving challenges (for the most part to see how inefficient I am in comparison)
The best part of doing CTFs? Learning more tools, gaining more knowledge and knowing how prone to making mistakes you are as you get tired (just me, i will explain later).
For example, there's a Stolen Licenses challenge under the Wednesday Category
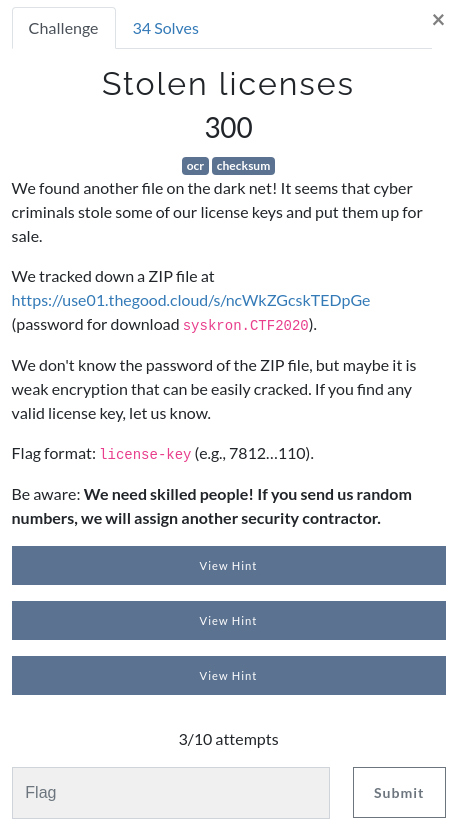
After downloading the zip file, inside are basically a bunch of images, the gist is that they are encrypted. It took way too long for me to actually even get the password.
I tried using JtR with the zip2john hash of the zip file with the famous rockyou.txt and various other files to no avail. So I ended up using the first hint (-30 points), which said key is probably a recently added word to a well known dictionary
So I went on and compiled a list of dictionary words recently added by Merriam-Webster, Dictionary.com as well as Oxford. But no, I still could not figure out the password.
Took me like 2 days later (I reached this question on the first day and got stuck) before I realised that my script used to grab the words had a mistake and that not every word was actually added to the list, you think that was my first mistake? No it was'nt, I only checked the script because I went to unlock hint number 2 (which had nothing to do with the password, wasted 30 points, actual mistake 1), and spent a goddamn 60 points for the last hint, which gave a link to recent added words on Merriam-Webster. Which is why I went through the script again...
On hindsight, I should have used something like cewl to make the word lists for me. After finally finding the password, which was nosocomephobia, a thousand images of the supposed keys greeted me. There is one out here that's valid, but I will have to check through all of them to find out.

Maybe unlocking the middle hint was not a mistake, as it mentioned something about check digits, in the very early trivia challenges, a question about the luhn formula used to check IMEI and other card numbers appeared.
However, we needed to extract the keys from the images in bulk, and convert them to text so we can perform checking somehow.
Long story short, we extracted them with a single bash script using imagemagick for cropping just the key portion and then using tesseract to ocr them to strings before running the luhn formula to get the one valid license and submit our flag.
I had never used imagemagick or tesseract before, so that's something learnt at least, and it was actually pretty fun.
I did not manage to solve any of the harder 500 points Friday challenges, but I am adamant on claiming that I did actually solve one in spirit. Let me explain.
There is this Firmware Update 500 point challenge with the following description
The crypto software LibrePLC at BB Industry is continuously receiving updates.
Unfortunately, the responsible employee left the company a few weeks ago and
hasn't deployed the most recent firmware with important security updates. He
just left a note with 5157CA3SDGF463249FBF. We urgently need the new firmware!
There were basically three different encrypted zip files provided. And that 5157CA3SDGF463249FBF was the key for the first zip file which gave us a a key file which was a python script and a LibrePLC_fw_1.0.0.bin file or the first firmware
The correct way to solve it can be found at https://ctftime.org/writeup/24354, the summary is that we were supposed to run the python script by passing in the LibrePLC_fw_1.0.0.bin file to get the password to the 2nd zip and use the same script on the LibrePLC_fw_1.0.1.bin inside the 2nd zip to get the password for the third zip which gives LibrePLC_fw_1.0.2.bin and then the flag was just hidden as string in LibrePLC_fw_1.0.2.bin, that is so easy, isn't it?
But dumb me decided to run the python script on the first zip instead of the bin file instead, and tried to use the password on the 2nd zip, failed, gave up and decided to start coding for my capstone project.
Dumb ways to die indeed.
The entire CTF was really fun, my only gripe? The supposed harder challenges actually took less time for me compared to the harder ones, specifically the 400 vs 300/200 points category, and I am not sure if its because I am more used to the tools used for the 400 point category or that it was indeed easier.
That's a pretty long rant.
TLDR you say? Here you go
TLDR:
- Join CTFs, they are fun, no matter how bad you think you are
- Do things at your own pace, even if you did not solve any challenge, its the process that counts
- Take your own notes or writeups during the CTF
- Compare your solutions to others to learn and read those you could'nt solve
- You get better with experience and learning from you mistakes